Name of patent
Patent No./Acceptance No.
A zero-loss data backup method and system
2013101570192
A hot backup method and system of MySQL database
2016107643078
A method for synthetic backup and instant recovery of database
2017103978518
A real-time database real-time backup method
2017103977445
Synthetic backup method and devices of MySQL database
2018111593600
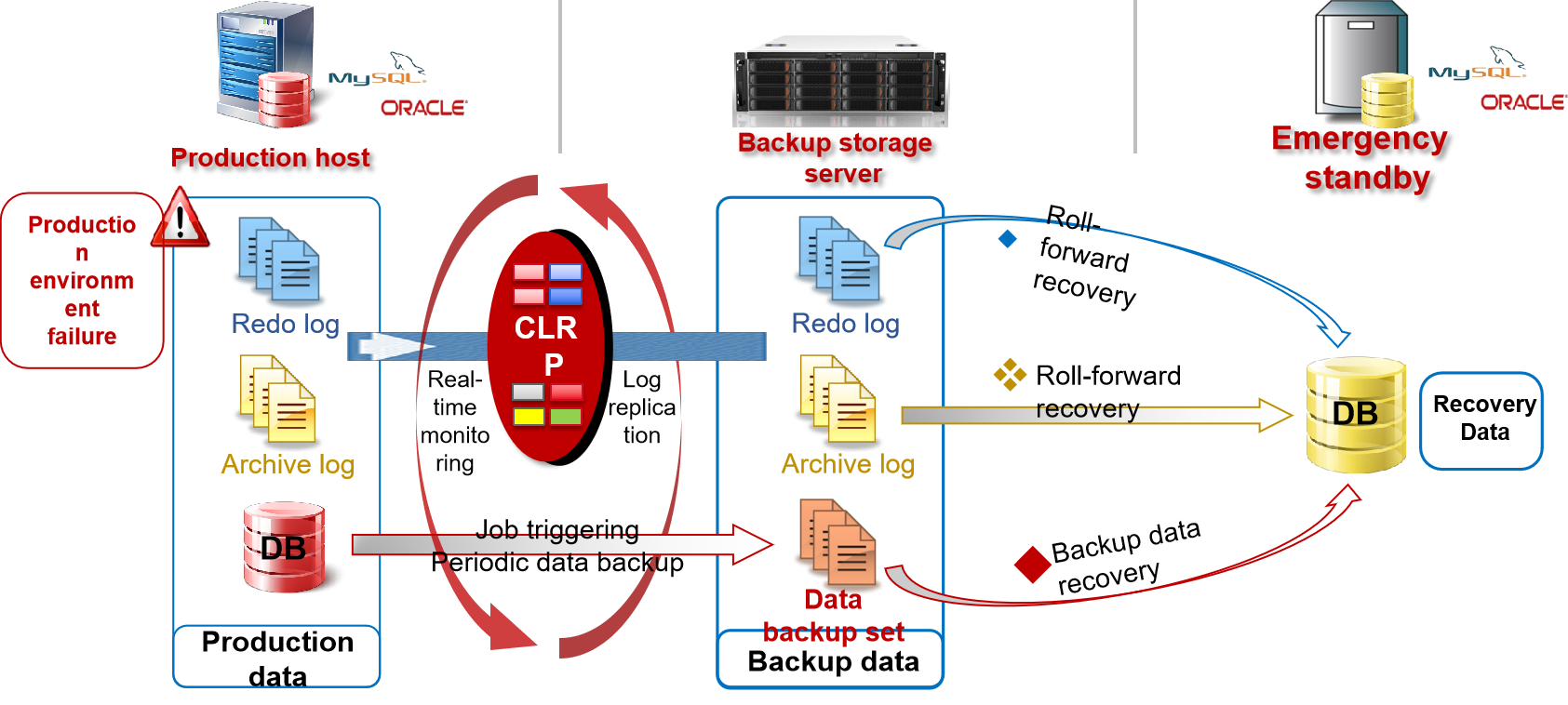
-
Reduces RPO to seconds with an average of 0.2 second a under normal load.
-
No soft or hard driver is needed which will not affect the running of the business system.
-
Variable data blocks which are replicated in real time are very small, so the resource usage is superior to CDP.
-
Backup transaction consistency is ensured, enabling restoration to any point in time or SCN.

The importance of housing fund information is undoubtful. It integrates ID, phone number, home address and payment information of each and everyone involved. Any information leak could expose such private information to criminals to conduct credit card theft or any other criminal activities.
The Housing Fund Management Center is responsible for collecting and managing housing fund information. A system breakdown caused by technological failure, corrupt device, maloperation, disasters or other accidents could divulge private information, disrupt business or even contribute to criminal activities.
Scutech has won the bid for Dingxi City Housing Fund Management Center in Gansu Province with its advanced R&D capability and customized a comprehensive data protection solution for the center.

The center undertakes payment and approval of use of housing fund within Dingxi city. It used to deploy an Oracle database on an AIX machine, any failure of which could immediately disrupt business or even lose data.

-
Server breakdown
As its key business data are all stored on an AIX server, the odds of hardware breakdown would significantly increase with years passing by. It is not impossible that data could be lost as a consequence.
-
The previous backup method is simple, complex and not efficient.
It previously wrote scripts to perform timely backup, which requires rather expertise.
-
No off-site disaster recovery
All important business data could be at stake in case of a disaster in the local data center.
-
No automated disaster recovery drills
Data availability cannot be verified.

The solution deploys DBackup and an IBM x86 server to provide automated real-time protection for Oracle database on the AIX machine. It will automatically perform full and incremental backup and uses data compression and deduplication technology to improve backup efficiency.
Create a same Oracle database environment as the Dingxi machine room and build a database synchronization system with the Oracle database in Dingxi data center through DBackup, data will be synchronized for off-site disaster recovery to prevent data loss due to a disaster.
Meanwhile, its disaster recovery drill module can back up important data to the disaster recovery drill server on a timely basis to verify data availability.
It also features a wizard design UI that is simple to use and allows users to deploy backup/recovery strategy within 6 steps.

Achieved…
Automated backup and recovery of Oracle database
Efficient real-time data backup and recovery
Off-site disaster recovery
Disaster recovery drills to verify data availability
Ensured independency and controllability with domestic backup and disaster recovery products

Recently, the MOHURD (Ministry of Housing and Urban-rural Development of the People's Republic of China) has issued a Guideline on Informatization Construction of Housing Fund Information, which explicitly states that the departments should build an information system with storage and devices that meets not only current demands but also future needs. It also states that departments should purchase domestic products and services with advanced and mature technologies. Scutech, as the only vendor in China that can provide completely domestic all-in-one backup/recovery solution, will keep devoted to product research and technology innovation and serve as a data guardian.
For more information, follow us on Wechat and stay tuned!

]]>

Department of Land and Resources, is responsible for managing, protecting, planning and utilizing land, minerals, ocean resources and so on. The Bureau of Land and Resources of Changsha County (hereinafter referred to as ‘The bureau’) oversees all land-related functional departments and administrative enforcement departments in the county. It has been honoured with ‘Advanced unit’ and ‘Civilized unit’ for multiple times.
![]()
The information centre of the Department of Land and Resources of Changsha County is responsible for planning and carrying out construction of information system and network of land and resources.
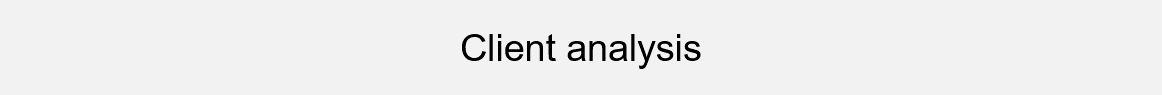
The bureau was instructed to implement a ‘Geospatial framework’ programme including an e-government platform and a private network for land and resources. The programme has several key business systems: a front-end WEB system, a back-end GIS system, a city-county integrated system, a sub-service system, a virtualization support system, databases and self-developed applications, which are based on two distinctive network segments on Windows, Linux, and VMware hybrid IT architecture. Any data loss could result in business downtime and incalculable economic loss. The challenge is to improve resource utilization ratio and optimize system performance meanwhile simplifying deployment and subsequent management process.

Adopts DBackup to separate backup pools and protect two major business platforms with one data protection system. Hosts in virtualization systems can be restored to the original or an alternate host without installing any agents. It also supports granular restore for files, making it much easier to deploy and more convenient to manage.
Our high-concurrency multi-channel technology significantly shortens backup period to just one hour, relieving pressure on production hosts. All backup data will be verified through a disaster recovery drill platform automatically to check its availability.

![]() Integrated backup under hybrid IT architecture, recovery drills
Integrated backup under hybrid IT architecture, recovery drills
-
Unified data protection under segmented network environment
-
Online protection under virtualized environment
-
Concurrent multi-channel backup of massive files
-
Automated disaster recovery drills
Its superior stability, security and agility have made it an excellent choice for multiple industries, for more information, follow us on Wechat and stay tuned!

]]>

Immovable property is an immovable object, an item of property that cannot be moved without destroying or altering it – property that is fixed to the earth, such as land or a house. Immovable property includes premises, property rights (for example, inheritable building right), houses, land and associated goods, and chattels if they are located on, or below, or have a fixed address.
Immovable property registration, as a means of property publication, is essentially a de facto act that will cause judicial effects. The executive meeting of the State Department explicitly states that the Ministry of Land and Resources oversees immovable property registration and construct a property registration system.
The Notice on Construction of Information Management Platform of Property Registration instructs that the information platform should be deployed on the ‘Land resource cloud’ built by the Ministry of Land and Resources and emphasizes the importance of adding information security on the agenda:
By the end of 2015, complete a trial run of the information platform;
By 2016, complete collecting and storing property registration data in a unified database;
By 2017, complete a nationwide deployment of property registration platform and accelerates the process of information platform construction;

 Demands
Demands
In new times, data security and high availability have become a matter of urgency as the State has issued a series of policies concerning informatization. With appliances aging and the lack of proper backup system, data loss could happen at any time. It is rather urgent to deploy a complete and secure HA information system to back up data.
 Targets
Targets
A complete, secure and high-availability basic architecture platform is built with Scutech products, integrating seamlessly with the existing virtualization platform of the client. It dynamically distributes resources on-demand for each application and maximizes computing resources with virtualization technology, which should cope with future demands in 3 to 5 years. HA of storage resources is realized with storage active-active technology. The system is scalable, stable and easy-to-maintain.
 General framework of the solution
General framework of the solution
![]() Service-level
Service-level
With virtualization technology, it distributes resources on-demand, guarantees elastic extension, exploits server performance, improves resource utilization and minimizes waste of resources; meanwhile, it adopts VMWare server cluster and vomtion technology to realize application HA.
![]() Storage-level
Storage-level
It uses InfoDitto and storage active-active technology to writes data into two Scutech storage appliances through a link replicator to ensure storage HA, which does not occupy host resources on production end and interfere with applications. In case of malfunction to the master storage, it can instantly switch to the secondary storage to ensure continuous operation.
![]() Data protection
Data protection
A unified backup platform to back up VMs, files, databases and operating systems. Customize your own backup policy and create a data protection policy to protect data integrity, confidentiality and availability.

-
Applies Scutech products to ensure seamless integration and optimize performance.
-
Realizes HA from application level to storage level to ensure RTO and RPO.
-
The solution is simple to deploy, easy to maintain and user-friendly.
The construction of a nationwide system of property registration followed by exponential growth of data will inevitably bring the question of how to protect national and personal data. Scutech, is devoted to developing reliable yet flexible data protection solutions to our customers.
For more information, follow us on wechat and stay tuned!

]]>

Schools, especially higher education institutions, are a cradle of national education, a base for scientific research, and the engine behind social progress. However, the importance of information security in higher education institutions has been substantially underestimated, leaving universities vulnerable to potential information invasion and leak and turning into a hunting ground for criminals.
Some might argue this is exaggerating. Well, let the sad facts talk. In May 2015, the Economic Information Daily combed through data from an anonymous loophole response platform and found out that between April 2014 to March 2015, there are up to 3,495 active loopholes on 1,088 university websites, in which there are 2,611 high-risk loopholes, taking up 74.7%, 691 mid-risk, 19.8% and 193 low-risk, 5.5%. Criminals may take advantage of the loopholes and tragedies happen. In Aug 2016, the whole nation was stunned at a girl, an about-to-be freshman of Nanjing University of Posts and Telecommunications got involved in a fraud and lost her tuition fees. She soon died of a heart attack on her way back home from the police station. Two days later, same thing happened again to another sophomore who also later died of a heart attack.
Unfortunately, such things happen more than just occasionally. In Nov 2016, a 10GB zip file swept across the internet containing nude photos and videos of female college students and was sold to netizens ranging from ¥50 to ¥100 per pic. Around 167 female students from 25 universities were involved, including their personal info, contact details of their close ones, and a naked picture of themselves holding their identity card.
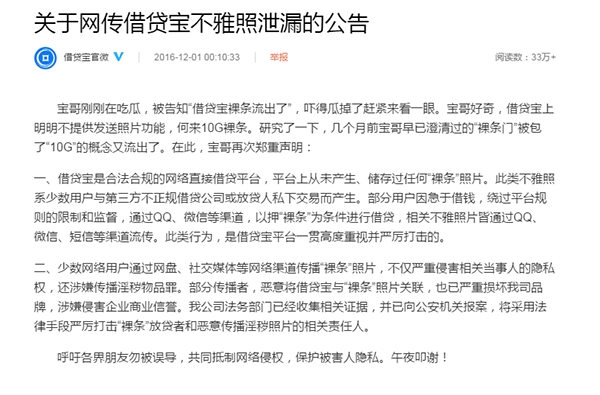
Information leak through loopholes in university websites is undoubtedly, the best feeding a criminal could ever ask for.
On one hand, with the campus system covering a wider range of services such as teaching service, scientific research, student life and administration, both the faculty and students heavily rely on it to conduct academic work, put in for teaching resources, arrange/submit assignments and even purchase groceries. Any malfunction to the system can affect normal operation of the university.
Worse still, it may leave confidential data of important scientific projects vulnerable to potential invasion. The results can be unbearable.
On the other hand, data security in universities are not attached enough importance as network security construction. Some universities don’t even back up their data or simple back up certain business applications manually, which is lengthy and cannot guarantee a successful recovery.
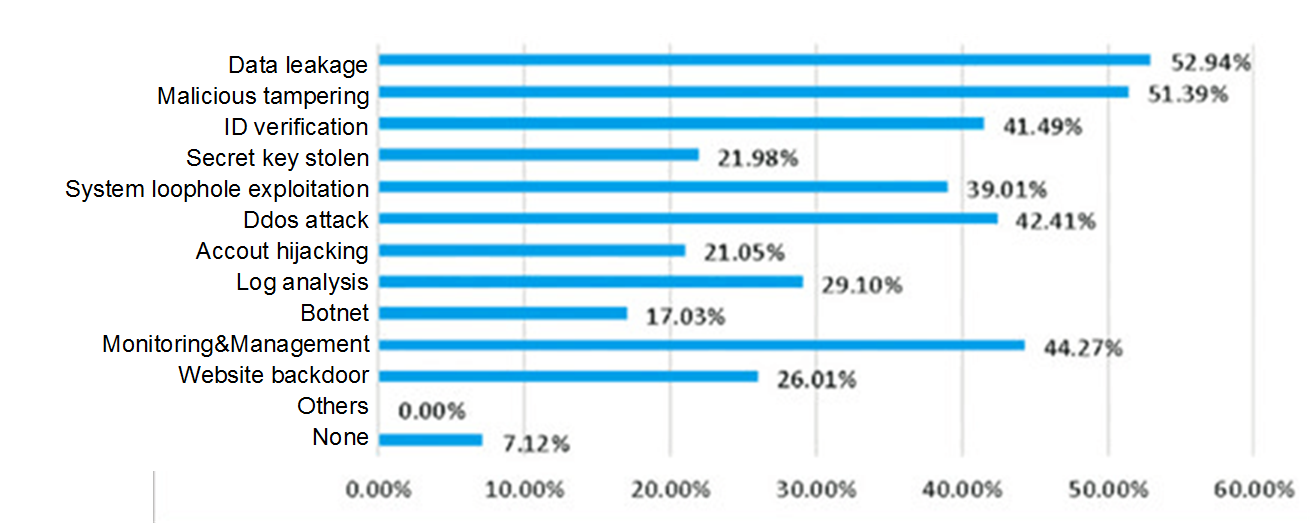
Information security demands of universities

|
The College of Humanities & Sciences of Northeast Normal University has several systems like the system for course selection, system for certification, system for scientific research and an official website. Services are put online, but without any protection. data is growing exponentially. Incidents like viruses, maloperation, malicious tampering with course scores, could corrupt data or even paralyze the system. Therefore, it is extremely important to address backup and recovery issue of the system.
As there are different OSs and application architecture in the production system, heterogeneous backup should be deployed.
Provides a user-friendly interface that allows operators to easily understand the process and configure and complete backup easily.
One of the main purposes of a backup system is to provide data protection for the business system, which makes stability and reliability a critical quality of a backup product. The software must be 100% compatible with OS and application systems in order to successfully back up and restore data in case of a disaster.
Off-site replication should also be enabled to make sure important data can be retrieved either from a local or off-site storage for quick recovery.
A cost-effective solution to safeguard the ever-growing hosts and applications in an information system.
Scutech deploys a turn-key data protection solution with InfoKist to meet data protection demands. The solution is also open for future expansion. Topology is as follows:
Install backup clients on production servers (such as: course selection system, certification system, scientific research system, the website), connect InfoKist to user network, set up backup policy, then InfoKist will automatically start backup according to the strategy and transfer backup data to InfoKist.
InfoKist restores data quickly and saves users from a tedious reinstallation and reconfiguration process of applications.
As a professional all-in-one hardware-software appliance, InfoKist costs less and is easy to manage.
Its HA architecture and off-site disaster recovery feature improve system availability, enhance business continuity and ensure uninterrupted operation of key applications. It also applies multiple security technologies and data protection measures to significantly improve security and guarantee smooth operation of business systems. As a member of state team of information security, Scutech is committed to scientific innovation in education industry, assist in informatization of universities and create a shield of data security for universities! For more information, scan the QR code below and follow us on wechat!
|

China has one of the world’s lowest crime rates. A study by ECNU (East China Normal University) reveals that: Crime rate in China, namely the number of criminal events happened in every 10,000 people in a year, accounts for only 360 per 10,000: only 3% of Switzerland, 3.25% of New Zealand, 3.5% of Finland, 3.8% of Denmark and 5% of America. For example, crime rate in Shanghai is lower than Munich, the alleged safest city in Germany. Other cities such as Beijing and Guangzhou also exhibit a higher safety index than other countries. For that, we owe it to our public security system that has done substantial work to maintain social security and stability, such as:

![]() A dense web of monitors has been knitted to watch out for our citizens and prevent criminal activities in advance. In 2010 alone, 10 million new monitors have been put in use.
A dense web of monitors has been knitted to watch out for our citizens and prevent criminal activities in advance. In 2010 alone, 10 million new monitors have been put in use.
![]() Quick police response. If someone dare molest another in a bus, simply dial 110, the police will show up at next bus stop to apprehend the suspect. In Beijing, it has specified on how fast local police should respond to an emergency report. Police should arrive in 5 minutes after they receive an emergency report in the eight urban areas and central areas in rural areas and towns, 10 minutes in urban and rural copula and outskirt areas. For remote rural areas and mountain areas, though time limit has not been given, the police should arrive as soon as possible.
Quick police response. If someone dare molest another in a bus, simply dial 110, the police will show up at next bus stop to apprehend the suspect. In Beijing, it has specified on how fast local police should respond to an emergency report. Police should arrive in 5 minutes after they receive an emergency report in the eight urban areas and central areas in rural areas and towns, 10 minutes in urban and rural copula and outskirt areas. For remote rural areas and mountain areas, though time limit has not been given, the police should arrive as soon as possible.

What a robust big data solution can offer for our public security is unimaginable. With data growing rapidly to TB or even PB level, it has brought new challenges and higher requirements upon system application and management than any other traditional backup assignment. A public security system contains a wide array of data types: videos, criminal information and so on. Such data is of great value to maintaining our social security and must be protected 24*7.
The public security IT system has built a mature data center in 2006. Its internal structure is super complex and contains many vertical applications. As new technologies like mobile internet and IoT(Internet of Things) have diversified data source, data relations become even more complicated. Also, as a special proprietary network designed for safeguarding social security, it needs to frequently interact with other data systems to retrieve information and coordinate operations. For example, if a driver from Guangdong province broke traffic rules in Beijing, the authority has to go through a lot of procedures to extract data.
For another example, during a financial fraud investigation, if you input a name and search citywide, the list may be short; but if you widen you search to nationwide, the result may be overwhelming. More tech issues will surface with time going on.

New changes have brought along new challenges, which a traditional technological approach cannot tackle. Not long ago, a tech expert working for a public security IT system shared his work experience. The public security system can be divided into:
![]() Social security related business system,
Social security related business system,
![]() Criminal related business system,
Criminal related business system,
![]() Economic investigation related business system,
Economic investigation related business system,
![]() Transport related business system,
Transport related business system,
![]() Command related business system,
Command related business system,
![]() Video business system.
Video business system.
In terms of data storage, data will be stored at where it is produced. To be specific, data produced from a municipal system will stay within this city, data produced from a provincial system will be stored by this province, data from a ministerial system will be stored by the nation.
Data reuse can be categorized into three levels:
Internal reuse: general queries, data replication, database account, and content search
Cross-region reuse: service request, whole-network search, check and verify
External reuse: cross-departmental information share, government website, people’s livelihood
“From my point of view, there is no critical difference between 1 million and 100 million data. Public security data is experiencing an exponential growth.”
Traditional technologies have hit its bottleneck as it can no longer realize computing models of current software. To bridge between public security network with government websites and other systems, it involves not only the pile-up of pics, videos and other forms of traditional business data, but also application of modern technologies such as distributed storage, graphical display, in-memory database and so on. “Upon such urgent demands, the public security system should join hands with more software developers and IT providers to resolve this issue together” as is addressed by the expert.
We had handled a project in public security system not long ago. The Bureau of Public Security of Province A was looking for a system featuring local backup with off-site synchronization to storage media.

The Bureau of Public Security in Province A has two major database systems: the basic platform database integrates information resources from all police divisions in the province, consisting of two Linux physical servers connected by Oracle RAC; the macro information database collects business information from all public security systems, also consisting of two Linux physical servers connected by Oracle RAC. Note that any malfunction to these two databases should be reported to Ministry of Public Security, so an all-round protection should be deployed to prevent any accidents.
However, there may be such problems as:
I) Possible damage to key business system server
Its key business systems (macro information database, basic platform database) all run on a X86 Linux server. Though Oracle RAC is deployed, considering the ratio of a X86-architecture server going south increases dramatically after a few years of use, there may be circumstances that all x86 servers malfunction at the same time and result in data loss.
II) It used to adopt a single and old-fashioned backup approach that is neither efficient nor user-friendly
III) It had no off-site disaster recovery. Once an emergency or disaster happens to local data center, partial or all business data may be lost.
IV) It had no automatic disaster recovery drills. No disaster recovery drills means there’s no way to verify the availability of backup data.
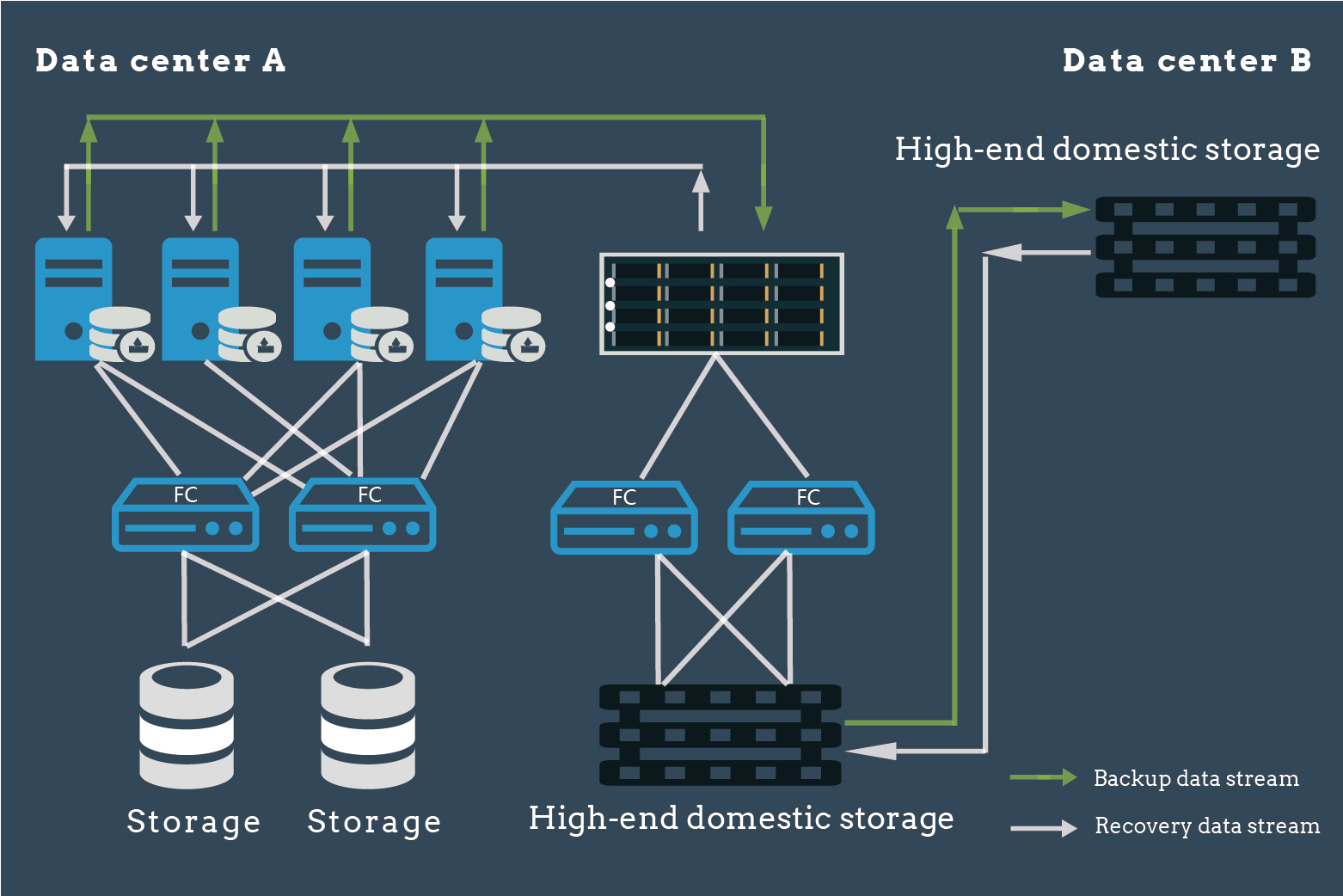
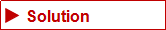
![]() The data center has purchased high-end domestic backup appliances, storage media and DBackup. With independently developed hardware-software, both key systems and Oracle RAC databases can be protected real-time.
The data center has purchased high-end domestic backup appliances, storage media and DBackup. With independently developed hardware-software, both key systems and Oracle RAC databases can be protected real-time.
![]() Automated full/incremental backup with compression and deduplication features to improve efficiency
Automated full/incremental backup with compression and deduplication features to improve efficiency
![]() Deploy appliances in the disaster recovery center to realize asynchronous synchronization with the other data center, backup data in the local backup media will be transferred to the other local center for off-site backup and avoid potential data loss.
Deploy appliances in the disaster recovery center to realize asynchronous synchronization with the other data center, backup data in the local backup media will be transferred to the other local center for off-site backup and avoid potential data loss.
![]() ‘Disaster recovery-Disaster recovery drill’ feature periodically restores important backup data to the server to verify its availability.
‘Disaster recovery-Disaster recovery drill’ feature periodically restores important backup data to the server to verify its availability.
![]() A user-friendly interface and a wizard to allow users to deploy within 6 steps.
A user-friendly interface and a wizard to allow users to deploy within 6 steps.


![]() Achieved automated backup and disaster recovery of databases
Achieved automated backup and disaster recovery of databases
![]() Achieved efficient real-time backup and recovery
Achieved efficient real-time backup and recovery
![]() Achieved off-site disaster recovery
Achieved off-site disaster recovery
![]() Achieved disaster recovery drills to verify data availability
Achieved disaster recovery drills to verify data availability
![]() Uses domestic hardware/software to ensure independence and controllability
Uses domestic hardware/software to ensure independence and controllability
An efficient and robust big data solution for public security should be able to integrate all kinds of data sources to assist the bureau in terms of information detection, analysis and decision-making, command and management, investigation and society service. Scutech, a safeguard of your public security data system, is there for you!

]]>
![]() ‘Accurate’
‘Accurate’
Variable-length partitioning and accurate deduplication
Scutech applies variable-length partitioning for non-structured data especially for backup of massive small files. Due to frequent changes of small files, a fixed-block partitioning will often result in repartitioning the whole backup, while variable-length partitioning targets only changed data, which occupies less computing resources and obtains optimal deduplication result as well.
 ‘Fast’
‘Fast’
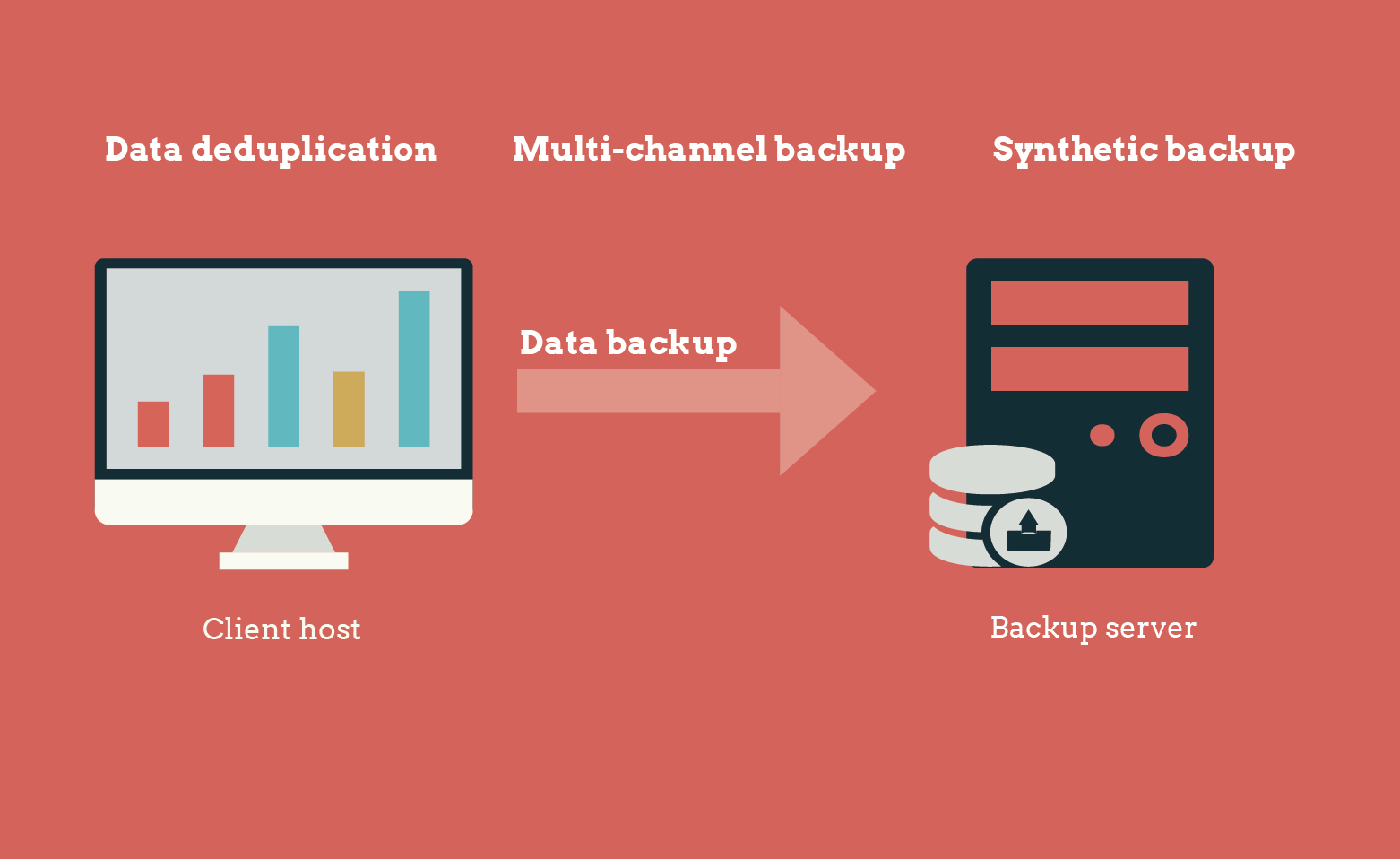
Multi-channel parallel backup improves efficiency
Scutech applies paralleling processing of file indexing and data backup and parallel data acquisition across multiple channels to significantly improve efficiency. Take a reservoir for an example, draining a reservoir through several water pipes is undoubtedly much faster than through a single pipe.
Parallel processing of file indexing and data backup
A traditional approach to GB-level file backup is to do a serial processing in one process: traverse files to back up, create a file index, then perform file backup. However, for massive files, as there could be a huge number of small files and a complex directory tree, it might consume too much time simultaneously traversing and indexing files, in other words, not efficient.
Scutech isolates file indexing and data backup into two separate processes: while the system is traversing through file directories, on one hand it creates an index for files and backs up files at the same time, which greatly shortens backup window and improves efficiency.
Parallel backup across multiple channels
To acquire and process files before backup, DBackup adopts multi-channel parallel technology that allows the system to firstly traverse through files using pipelining technology, create a file index, shard file information, then transfer backup data through multiple backup channels to the storage server.
The difficulty lies in determining a proper strategy to distribute sharded dataacross multiple channels and integrating backup sets during recovery. Scutech developed an algorithm to automatically monitor channel usage and distribute backup data across unoccupied channels. During recovery, it restores data to its original directory in an efficient and secure manner.
![]() ‘Less’
‘Less’
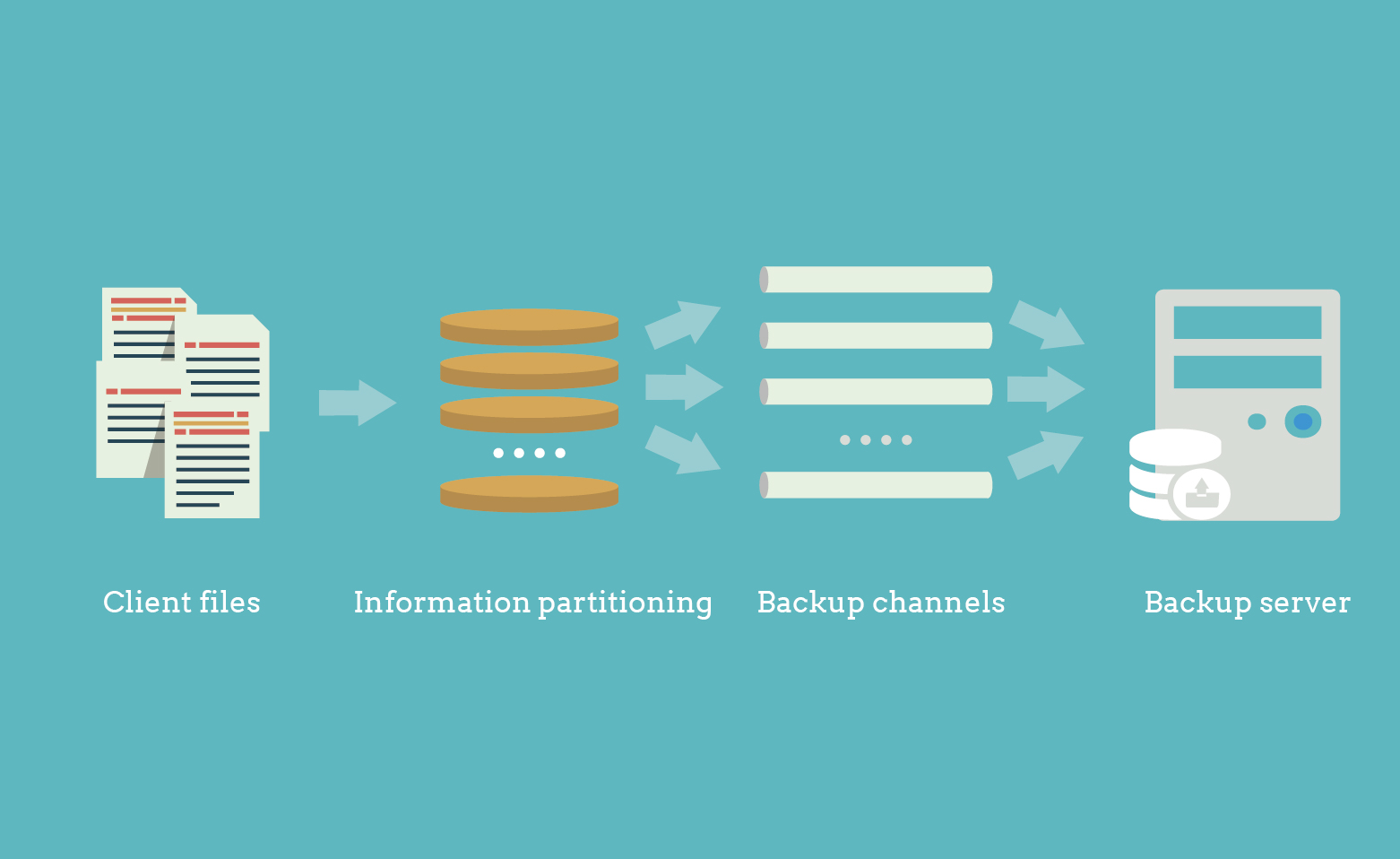
Automated synthesis on server-end, lessening resource occupation
An optimal backup strategy for massive files, especially small files. Compared with a traditional periodic backup approach that periodically performs a lengthy ‘full+incremental backup’, which consumes many computing, I/O and networking resources and interferes with key operations, DBackup synthesizes the initial full backup with subsequent incremental backups to generate a new full backup. Then it again synthesizes with a new incremental backup to generate a newer full backup. The cycle repeats itself. Our file synthetic backup supports all major platforms and environments, including file backup through a mounted disk in NFS or CIFS(Volume-level CDP technology does not support this feature yet).
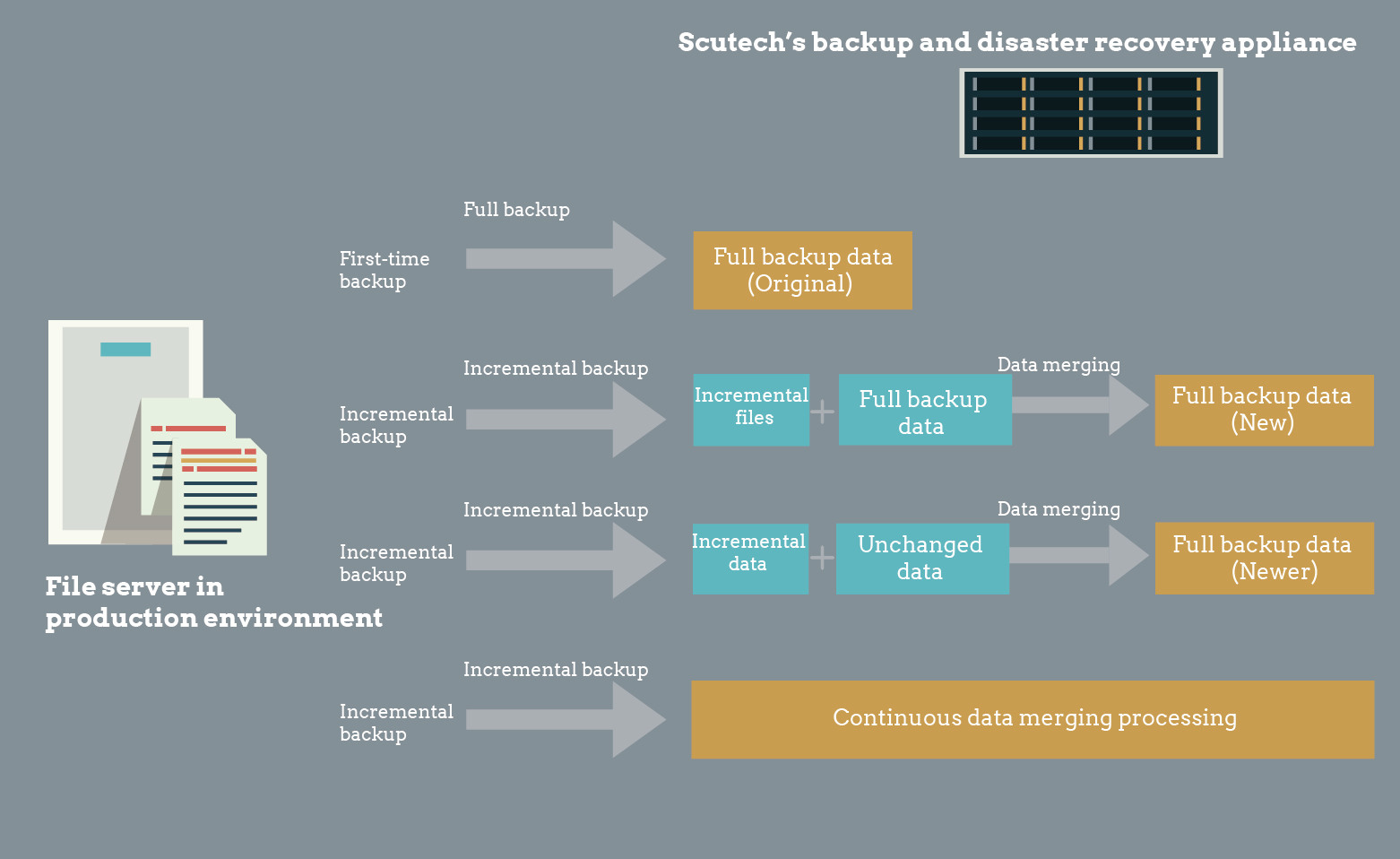
DBackup integrates multiple technologies to deliver an accurate, fast and efficient backup of massive small files. For more information,scan or long-press the QRcode below and follow us on wechat!
Director: Action!
Shopping adviser: Sir, what are you looking for?
Customer: I am looking for a backup and CDP device.
Shopping adviser: We have a disaster recovery software that includes backup and CDP.
Customer: I am looking for an all-in-one machine.
Shopping adviser: Okay, this one here is our all-in-one machine.
Customer: But wouldn’t they fight for resources if they are all stuffed in one machine.
Shopping adviser: Well, how about a backup all-in-one and CDP all-in-one? They won’t fight for resources and still integrate all features needed.
Customer: This way it will increase cost and add burden on management.
Shopping adviser: Sorry, I don’t think there are any other products in the market that meet your demands.
Director: Cut! According to the latest news, Scutech is about to release three new InfoKist models. You can have it both ways now!
Headline today
New InfoKist models, including InfoKist-DKC (Backup plus CDP), InfoKist-DKH (Backup plus HA) and InfoKist-DKT(Backup plus Takeover) will be released REAL SOON!!!
It has two different deployments:
Deployment I has: 2U+Dual-node server, Intel G612 high-performance Chipset, 48G memory, up to 12 3.5’’ hot-pluggable SATA/SAS hard drive and 6*1G Ethernet.

Deployment II has: 2U+dual-node server, Intel G612 high-performance Chipset, 64G memory, up to 32 2.5’’ hot-pluggable NLSAS hard drive and 6*1G Ethernet.

The new InfoKist models deploy shared architecture with shared battery, heat dissipation, management and bandwidth to achieve high efficiency. With our new InfoKist models, you can enjoy:
 Backup: focuses on protection of massive data across files, databases, applications, operating systems and VMs. In case a disaster strikes, it will restore data quickly, accurately and completely to minimize economic loss of enterprises.
Backup: focuses on protection of massive data across files, databases, applications, operating systems and VMs. In case a disaster strikes, it will restore data quickly, accurately and completely to minimize economic loss of enterprises.
 CDP: continuous protection of volume-level data. Captures change of logs in the system and stores them on the backup appliance, which can be used to perform point-in-time recovery in case of a data disaster to meet higher RTO and RPO requirements.
CDP: continuous protection of volume-level data. Captures change of logs in the system and stores them on the backup appliance, which can be used to perform point-in-time recovery in case of a data disaster to meet higher RTO and RPO requirements.
 HA: Shared/mirror HA-clustering solution to build a multi-node clustering environment and server takeover mechanism to ensure 24*7 uninterrupted operation and avoid potential data and economic loss due to SPOF.
HA: Shared/mirror HA-clustering solution to build a multi-node clustering environment and server takeover mechanism to ensure 24*7 uninterrupted operation and avoid potential data and economic loss due to SPOF.
Achievements
 Simplified deployment and management process. As the device integrates two servers added with backup/CDP/HA features, it is deployed and managed as one machine, allowing users to manage the appliance effortlessly.
Simplified deployment and management process. As the device integrates two servers added with backup/CDP/HA features, it is deployed and managed as one machine, allowing users to manage the appliance effortlessly.
 Optimal utilization of resources. Our new InfoKist models is an agile yet efficient platform to share storage and network resources between nodes. Resources are adjusted real-time for eachassignment and utilization ratio is improved.
Optimal utilization of resources. Our new InfoKist models is an agile yet efficient platform to share storage and network resources between nodes. Resources are adjusted real-time for eachassignment and utilization ratio is improved.
 Reduced cost. Significantly reduces initial purchase expenditure, space occupation, electricity consumption and OAM cost.
Reduced cost. Significantly reduces initial purchase expenditure, space occupation, electricity consumption and OAM cost.
![]()
Director: Action!
Shopping adviser: Let me guess, you are looking for a device that integrates two modules in one appliance and is simple to deploy and manage. Here is the recently released InfoKist models by Scutech Corporation with backup and CDP(or HA, takeover if you prefer) embedded in one.
Customer: Very well…

![]() Demands
Demands
As Guangdong Provincial E-government data center stores data of various government departments and backs up e-government cloud platform, it is crucial and of great urgency to build an off-site disaster recovery center to prevent potential data loss in case of a natural disaster, fire, or other unpredictable scenarios. The off-site center should be located at least 100 km away from its local center in Guangzhou and is responsible for constant backup of business data to ensure data security.
![]() Purpose
Purpose
The solution should realize off-site disaster recovery of provincial e-government data; it should also meet level-3 requirement of Classified Protection of Information System Security and level-4 of Specification for Disaster recovery of Information Systems to improve data security and ensure business continuity.
![]() Solution
Solution
Deploy InfoKist on each center and connect via a dedicated government network to ensure government data security across various regions.
A PB-class backup data storage pool to protect massive government data including files, databases, OSs, VMs and office applications.
Remote backup data replication and deduplication technology plus a dedicated secure network restores data remotely in case of a disaster in local center.
A disaster recovery management platform to manage backup resources and systems in different regions and integrate information such as job progress, backup data statistics and reporting to ease the burden on maintenance personnel.

(↑: equipment assembled, tested and ready to be delivered to client)
Protect e-government system in case of system malfunction and data corruption and restore it with the latest copy and archive data in a quick and safe manner. The solution has met level-3 requirement of Classified Protection of Information System Security and level-4 of Specification for Disaster Recovery of Information Systems.
The console monitors and manages client resources, backups, jobs and alerts from various regions and by integrating and analyzing such information from multiple dimensions and displaying results in a graphical way, it simplifies management process and reduces workload of personnel. Such solution can well adapt to the large yet complex production environment of the e-government system and meet a higher disaster recovery management standard.
]]>
![]() Demands
Demands
![]() Major business systems including but not limited to HIS, PACS and EMRS should be protected.
Major business systems including but not limited to HIS, PACS and EMRS should be protected.
![]() SQL Server database and PACS files should be backed up and synchronized.
SQL Server database and PACS files should be backed up and synchronized.
![]() Issues
Issues
![]() Currently users use scripts to back up data and it requires frequent human interference during recovery process and the result may still not be as expected.
Currently users use scripts to back up data and it requires frequent human interference during recovery process and the result may still not be as expected.
![]() Supports only point-in-time backup
Supports only point-in-time backup
It currently only performs periodical incremental backup and data synchronization is not realized between master and standby databases. Once the master database malfunctions, it will take forever to recover and data loss can hardly be avoided.
![]() Lack of a unified console
Lack of a unified console
As backup is currently done manually, there is no unified console for users to review transaction and monitoring logs.
![]() No disaster recovery drills
No disaster recovery drills
Availability of backup data cannot be verified.
![]() Solution
Solution
![]() Deploy DBackup in machine room to protect PACS, HIS and EMRS. Backs up and manages files, databases and operating systems of the hospital on one console.
Deploy DBackup in machine room to protect PACS, HIS and EMRS. Backs up and manages files, databases and operating systems of the hospital on one console.
![]() Multi-channel backup, which significantly improves efficiency.
Multi-channel backup, which significantly improves efficiency.
![]() Synchronization between master and standby databases allows users to switch to the standby in case of malfunction of local database and business will not be interrupted.
Synchronization between master and standby databases allows users to switch to the standby in case of malfunction of local database and business will not be interrupted.
![]() Data deduplication from the source end reduces backup volume and network occupation.
Data deduplication from the source end reduces backup volume and network occupation.
![]() A database disaster recovery drill strategy will periodically recover the backup set to a server to verify its availability.
A database disaster recovery drill strategy will periodically recover the backup set to a server to verify its availability.
![]() A web console to manage backup and improve efficiency.
A web console to manage backup and improve efficiency.
![]() Solved…
Solved…
![]() Concerns over business data security of the hospital
Concerns over business data security of the hospital
![]() Efficient real-time backup and recovery
Efficient real-time backup and recovery
![]() Off-site disaster recovery
Off-site disaster recovery
![]() Verification of backup set availability
Verification of backup set availability
![]() User-friendliness of backup system
User-friendliness of backup system
